- HOME
- All Products
- Navigating email hazards: Phishing scams - upgrading your defence against digital deceivers
Navigating email hazards: Phishing scams - upgrading your defence against digital deceivers
- Published : November 10, 2023
- Last Updated : September 16, 2025
- 2.1K Views
- 14 Min Read
Phishing is a deceptive email-based attack that aims to trick recipients into taking certain actions or disclosing sensitive information. Attackers typically send fraudulent emails that impersonate trusted entities, such as banks, service providers, or colleagues. These emails often contain convincing messages and may include malicious links or attachments. Phishing attacks exploit human vulnerability and rely on psychological manipulation to deceive individuals into revealing passwords, financial details, or other confidential data. Successful phishing attempts can lead to identity theft, financial loss, unauthorized access to systems, and compromised accounts. Implementing strong email security measures and educating users about phishing risks are essential for mitigating this pervasive threat.
- Email spoofing: Attackers manipulate the email headers and sender information to make the email appear as if it comes from a legitimate source, deceiving recipients into believing it is trustworthy.
- URL phishing/link-based phishing: URL phishing involves the use of deceptive links in emails. Attackers include URLs that appear to be legitimate but actually lead to malicious websites designed to trick users into providing sensitive information, such as login credentials or personal details. These phishing URLs often mimic the URLs of well-known websites or online services to deceive recipients.
- Spear phishing: A targeted form of phishing where attackers tailor their messages to specific individuals or groups, using personalized information to increase the chances of success.
- CEO fraud/business email compromise (BEC): A sophisticated form of phishing that targets organizations, specifically executives or employees with financial authority, to trick them into authorizing fraudulent transactions or sharing sensitive company information.
- Credential phishing or account theft: Phishing attacks aim to steal login credentials, such as usernames and passwords, by tricking users into providing them on fake login pages or through other deceptive means.

Characteristics
These key characteristics help identify and understand the unique aspects of the different types of phishing attacks, allowing organizations to implement targeted preventive measures and enhance their email security defenses.
| Phishing type | Characteristics |
| Email spoofing |
|
| URL phishing/link-based phishing |
|
| Spear phishing |
|
| CEO fraud/BEC |
|
| Credential phishing/account theft |
|
Impact assessment
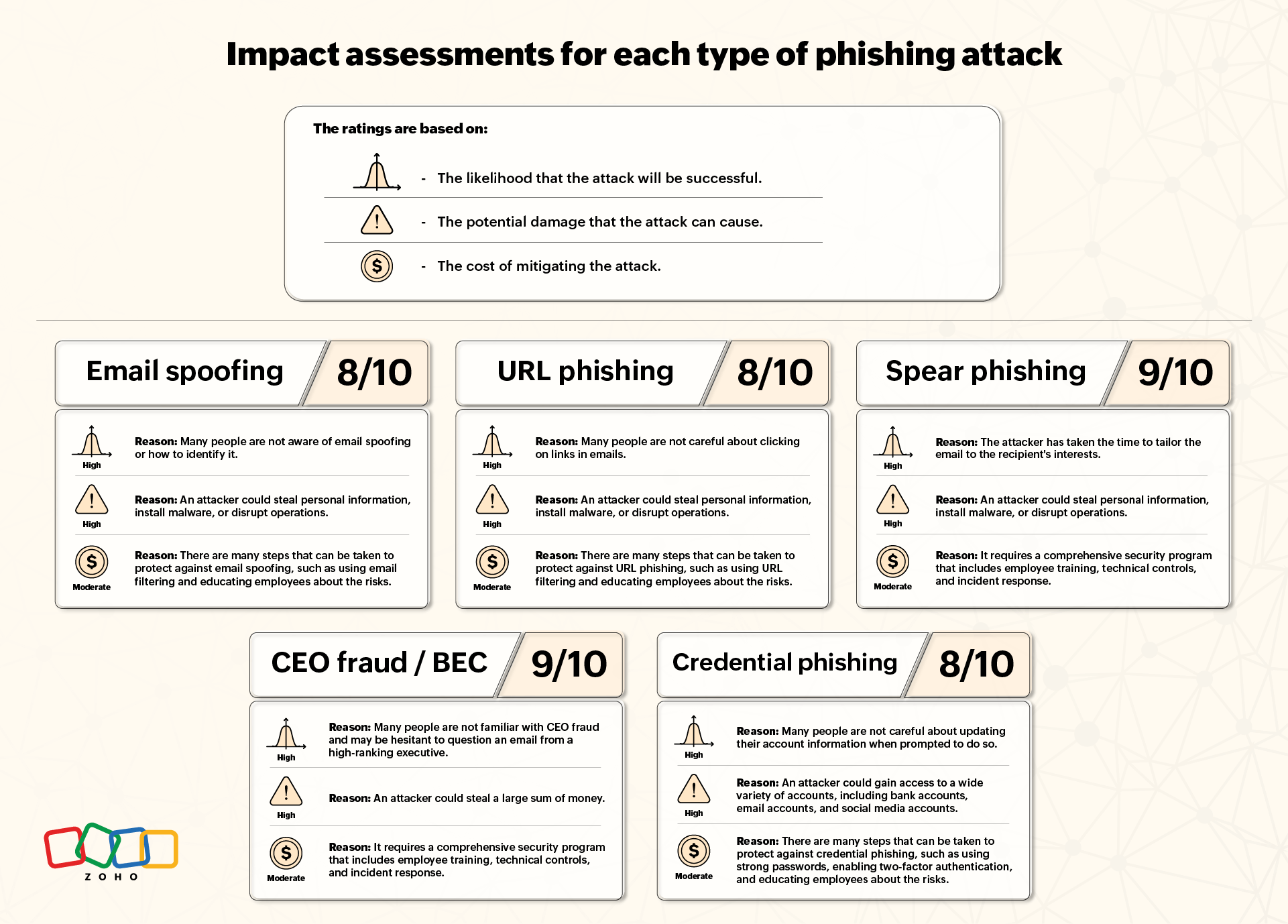
Attack vectors
In the context of email security, "attack vectors" typically refer to the different methods or avenues through which an attacker can exploit vulnerabilities or carry out an attack.
| Threat | Attack vectors |
| Email spoofing |
|
| URL phishing |
|
| Spear phishing |
|
| CEO fraud/BEC |
|
| Credential phishing |
|
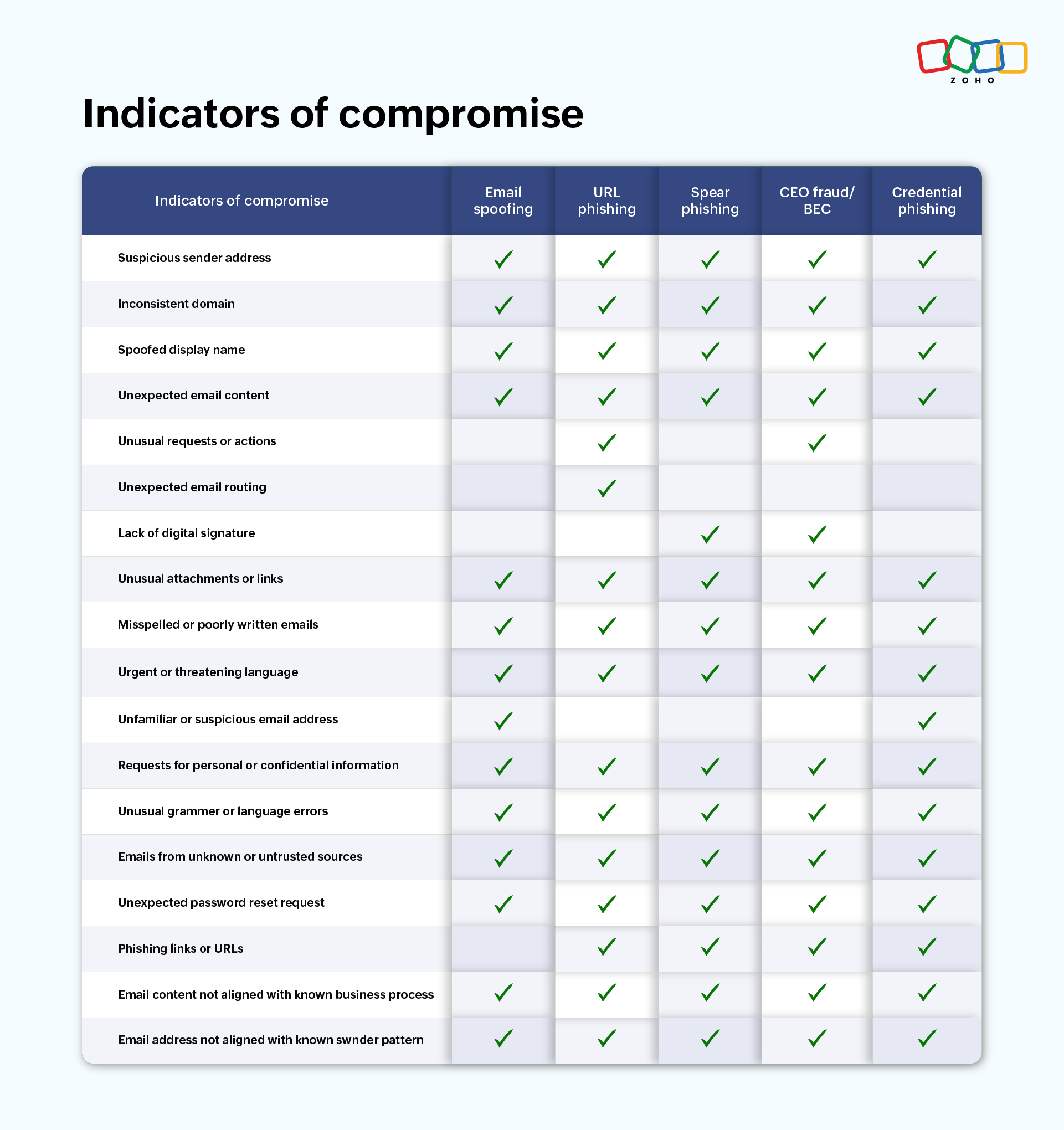
Indicators of compromise
Below are indicators of compromise that can be warning signs of potentially malicious or fraudulent email phishing attacks. It is essential for individuals and organizations to be vigilant and exercise caution when encountering emails exhibiting these indicators to prevent security breaches.
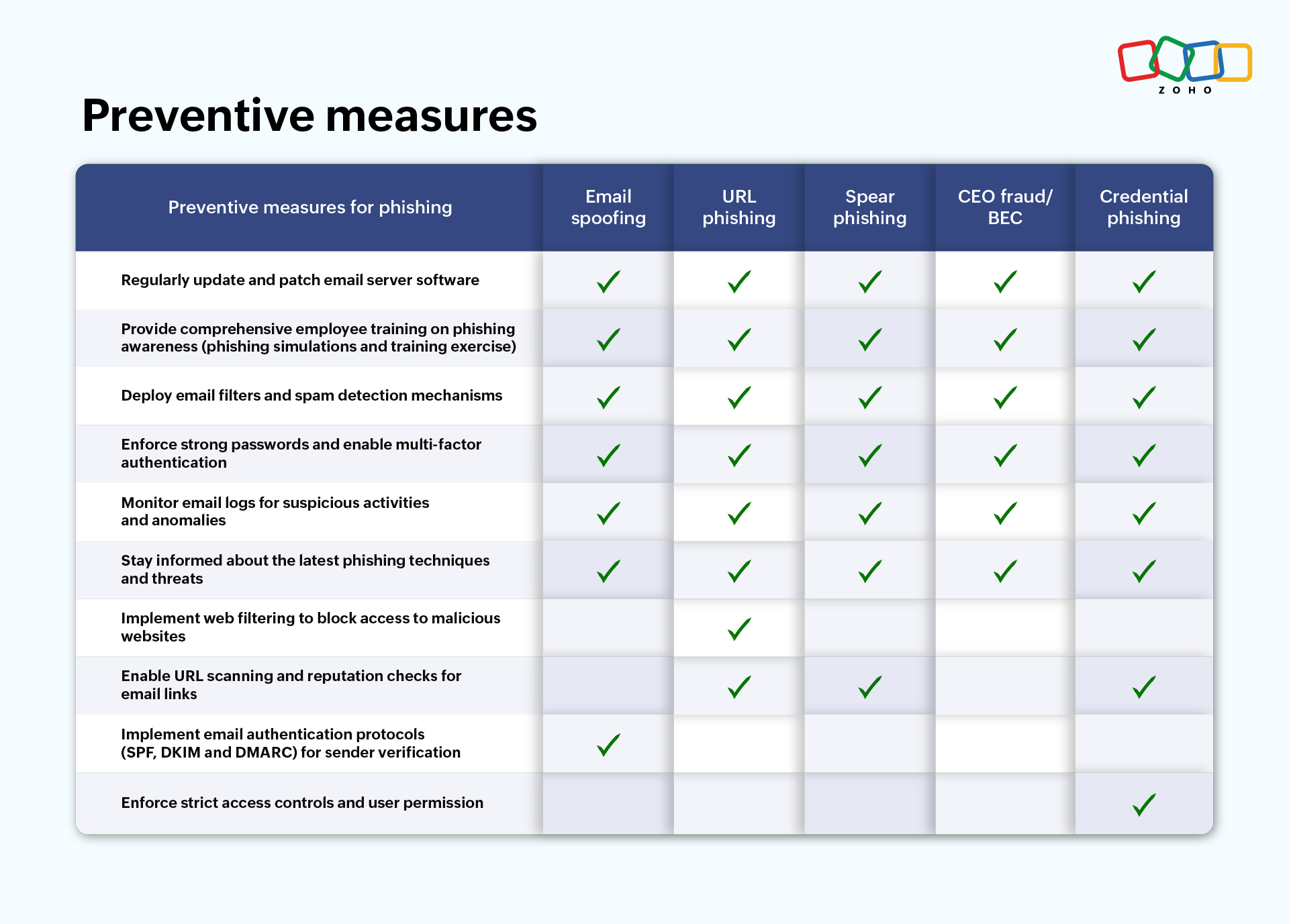
Preventive measures
By implementing preventive measures, organizations can effectively combat the different types of phishing attacks and enhance email security.
Detection mechanism
Here's a tabular form with the effectiveness of each detection mechanism for each type of phishing attack.
| Detection mechanism | Email spoofing | URL phishing | Spear phishing | CEO fraud/BEC | Credential phishing |
| Email header analysis: Analyzes email headers to identify anomalies, such as mismatched or forged sender information. | High | Medium | High | High | High |
| URL analysis: Examines URLs in emails to determine if they are suspicious or lead to known malicious websites. | Medium | High | High | High | Medium |
| Content analysis: Analyzes the content of emails, looking for phishing indicators like misspellings, grammatical errors, etc. | Medium | Medium | High | High | Medium |
| Sender reputation analysis: Assesses the reputation of the email sender, considering factors like email volume, history, and authentication. | High | Medium | Medium | High | High |
| Domain authentication: Verifies the authenticity of the sending domain by checking SPF, DKIM, and DMARC records. | High | Medium | High | High | High |
| Link reputation analysis: Evaluates the reputation of embedded links to identify potential malicious or phishing URLs. | Medium | High | High | High | Medium |
| User behavior monitoring: Tracks user actions and behavior to detect abnormal or suspicious activities related to phishing. | Medium | Medium | High | High | Medium |
| Anomaly detection: Detects anomalous patterns in email communication, such as unusual login locations or access attempts. | Medium | High | High | High | Medium |
| Fraud detection systems: Utilizing advanced algorithms and machine learning to detect fraudulent activities. | High | High | High | High | High |
Mitigation techniques
| Mitigation techniques | Email spoofing | URL phishing | Spear phishing | CEO fraud/ BEC | Credential phishing |
| Email filtering | Can block emails that are sent from spoofed email addresses. | Can block emails that contain malicious URLs. | Can block emails that are targeted at specific individuals or groups. | Can block emails that appear to be from a company's CEO or other high-ranking official. | Can block emails that request personal information, such as passwords or credit card numbers. |
| Employee training | Employees can be trained to identify phishing emails and to report them to IT security. | Employees can be trained to be wary of clicking on links in emails, even if they appear to be from legitimate sources. | Employees can be trained to be suspicious of emails that are targeted at them specifically. | Employees can be trained to report any emails that appear to be from the CEO or other high-ranking official to IT security. | Employees can be trained to never share their passwords or other personal information over email. |
| Multi-factor authentication | Multi-factor authentication adds an extra layer of security by requiring users to enter a code from their phone in addition to their password when they log in. This can help to prevent attackers from gaining access to user accounts even if they have successfully phished their passwords. | Multi-factor authentication can also help to prevent attackers from using stolen passwords to access user accounts. | N/A | N/A | N/A |
| Data encryption | Data encryption can help protect sensitive data from being stolen if an attacker does gain access to a user account. | Data encryption can also help protect sensitive data from being intercepted in transit. | N/A | N/A | N/A |
| Incident response plan | Outlines steps to address and mitigate phishing incidents. | Guides response to URL phishing attacks. | Provides guidelines for handling spear phishing incidents. | Offers a framework for responding to CEO fraud/BEC attacks. | Defines actions to take when responding to credential phishing incidents. |
| Account monitoring | Account monitoring can detect unauthorized logins from different locations, which may be a sign of email spoofing. | Account monitoring can detect unauthorized logins from different browsers or devices, which may be a sign of URL phishing. | Account monitoring can detect unauthorized logins from IP addresses that are not typically associated with the user, which may be a sign of spear phishing. | Account monitoring can detect unauthorized wire transfers or other financial transactions, which may be a sign of CEO fraud/BEC. | Account monitoring can detect unauthorized changes to passwords or security questions, which may be a sign of credential phishing. |
Reporting and incident response
| Attack type | Reporting and incident response for employees | Incident response for admins |
| Email spoofing | If an individual receives an email that looks suspicious, they should refrain from clicking on any links or opening any attachments. Instead, they should forward the email to their IT department or security team. | If an employee reports an email that they believe is a phishing attempt, investigate the email and take appropriate action. This may include blocking the sender's email address, quarantining the email, or notifying the sender's organization. |
| URL phishing | If an individual receives an email that contains a link to a website, they should avoid clicking on the link. Instead, they should manually type the website address into their browser. | If an employee reports an email that contains a malicious link, investigate the link and take appropriate action. This may include blocking the link, quarantining the email, or notifying the website's owner. |
| Spear phishing | If an individual receives an email that is specifically targeted to them, they should avoid clicking on any links or opening any attachments. They should forward the email to their IT department or security team. | If an employee reports an email that is specifically targeted to them, investigate the email and take appropriate action. This may include blocking the sender's email address, quarantining the email, or notifying the employee's manager. |
| CEO fraud/BEC | If an individual receives an email that appears to be from their CEO or another high-ranking executive, they should avoid clicking on any links or opening any attachments. Instead, they should contact the executive directly to verify the authenticity of the email. | If an employee reports an email that appears to be from their CEO or another high-ranking executive, investigate the email and take appropriate action. This may include blocking the sender's email address, quarantining the email, or notifying the CEO or other executive directly. |
| Credential phishing | If an individual receives an email that asks for their username, password, or other personal information, they should refrain from providing it. Instead, they should contact the organization that the email appears to be from to verify the authenticity of the request. | If an employee reports an email that asks for their username, password, or other personal information, investigate the email and take appropriate action. This may include changing the employee's password, resetting the employee's account, or notifying the employee's manager. |
Regulatory compliance considerations
Under regulatory compliances, organizations are required to implement appropriate security measures to protect personal data from unauthorized access, loss, alteration, or disclosure. This includes email communications because emails often contain personal data. They indirectly address phishing attacks by emphasizing the need for safeguards, risk assessments, training programs, and awareness about email security among employees. Organizations should consult the specific regulations applicable to their industry and jurisdiction to ensure compliance and take appropriate actions to mitigate phishing risks.
| Regulatory compliance | Relevant regulations or standards |
| General Data Protection Regulation (GDPR) | GDPR emphasizes the protection of personal data and privacy, which indirectly addresses phishing attacks as a threat to data security. |
| Payment Card Industry Data Security Standard (PCI DSS) | PCI DSS includes requirements for protecting payment card data, which can help mitigate phishing attacks targeting financial information. |
| Health Insurance Portability and Accountability Act (HIPAA) | HIPAA focuses on safeguarding electronic protected health information (ePHI) and requires measures to protect against unauthorized access, including phishing attacks. |
| Federal Trade Commission Act (FTC Act) | The FTC Act prohibits deceptive trade practices, including phishing attacks, and holds organizations accountable for ensuring the security and privacy of consumer information. |
| Sarbanes-Oxley Act (SOX) | SOX mandates internal controls and measures to protect financial information, which indirectly helps mitigate phishing attacks targeting financial data. |
| NIST Cybersecurity Framework | NIST provides guidelines and best practices for managing and securing information systems, which include addressing phishing threats and implementing appropriate security controls. |
| ISO 27001 | ISO 27001 is an international standard for information security management systems and includes measures to protect against phishing attacks through risk assessments, employee training, and incident response procedures. |
| Sector-specific regulations | Some industries have sector-specific regulations that address phishing attacks, such as the financial sector's regulations from regulatory bodies like the Financial Industry Regulatory Authority (FINRA) or the Securities and Exchange Commission (SEC). |
Case studies
These case studies demonstrate real-world examples of successful phishing attacks across different types, highlighting the impact and risks associated with each type of phishing technique.
| Phishing type | Case |
| Email spoofing | Snapchat employee payroll data breach: In 2016, cybercriminals targeted Snapchat through an email spoofing attack. They impersonated the CEO of Snapchat and sent an email to the company's payroll department requesting employee payroll information. The employees, believing the email was legitimate, provided the requested data, resulting in a significant data breach. |
| URL phishing | PayPal phishing scam targeting account credentials: In various instances, cybercriminals have conducted phishing attacks targeting PayPal users. They send fraudulent emails pretending to be from PayPal, directing recipients to a spoofed website that mimics the official PayPal login page. Unsuspecting users enter their login credentials, unknowingly providing them to the attackers. |
| Spear phishing | DNC email hack during the 2016 U.S. presidential election: During the 2016 U.S. presidential election, spear phishing played a significant role in the cyber attack on the Democratic National Committee (DNC). Attackers sent highly targeted and convincing emails to DNC officials, tricking them into disclosing login credentials. This breach resulted in the release of sensitive emails, impacting the election campaign. |
| CEO fraud/BEC | Ubiquiti Networks Inc. fraudulent wire transfer incident: In 2015, Ubiquiti Networks Inc., a networking technology company, fell victim to a CEO fraud/BEC attack. The attackers impersonated the company's executive and sent fraudulent emails to the finance department, instructing them to transfer a significant amount of money to a bank account. The company suffered millions of dollars in losses due to the fraudulent wire transfer. |
| Credential phishing | Google Docs phishing attack: In 2017, a widespread phishing attack targeted Google Docs users. Attackers sent emails appearing to be a Google Docs file-sharing invitation. Clicking on the link redirected users to a fake Google login page, tricking them into entering their credentials. This attack aimed to harvest user credentials and gain unauthorized access to Google accounts. |
This article is co-authored by Sandeep Kotla and Vignesh S.
Sandeep is an accomplished inbound marketer at Zoho Corporation, specializing in digital workplace strategies, digital transformation initiatives, and enhancing employee experiences. Previously, he handled analyst relations and corporate marketing for Manage Engine (a division of Zoho Corp) and its suite of IT management products. He currently spends most of his time re-imagining and writing about how work gets done in large organizations, reading numerous newsletters, and Marie Kondo-ing his inbox.
Vignesh works as a Marketing Analyst at Zoho Corporation, specializing in content initiatives and digital workplace strategies. He's a passionate creator with a penchant for marketing and growth. In his free time, you can see him shuffling between books, movies, music, sports, and traveling, not necessarily in the same order.


